Understanding SSL
Table of Contents
TODO
- https://www.ssl.com/article/what-is-a-certificate-authority-ca/#:~:text=The%20CA%20verifies%20the%20certificate,trust%20in%20the%20certificate's%20validity.
- https://www.digicert.com/blog/what-is-a-certificate-authority
How are certificate signing authorities used in companies?
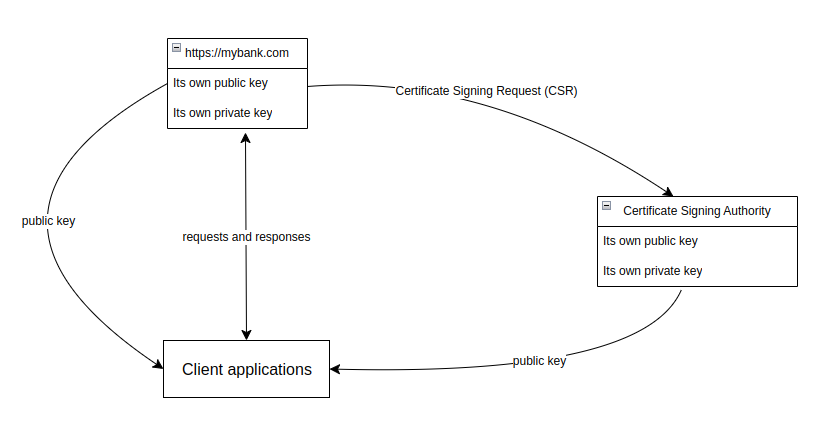
- The entity that wants to be secured will use its own private key and send a CSR (Cerficate Signing Request) to a Certificate Signing Authority (CSA).
- The CSA will use their private key to approve this CSR and they will give a
certificateto the requesting entity.
Examples of CSAs
- DigiCert
How will the client applications (the developer applications in developers’ local computers) connect to this secured entity?
- All of the client applications have the CSA’s public key.
- All of the client applications will also have the public key of the secured entity (the bank).
- Check the path
/etc/ssl/certsfor the list of available public keys that are being used by the local computers. - The client application needs to send a request to the secured entity with a key that is encrypted using the public keys of the CSA and the secured entity.
- Since the secured entity has a
certificatefrom the CSA and it’s own private key, it will use it’s private key and the certificate from the CSA to validate whether this request from the client application can be trusted or not. - This is how the communication between the client applications and the secured entity are protected/secured.
How to set this up for local computers for development purposes?
- We don’t have a CSA for local
- So we have to set-up our own certificates.
How do we generate certificates for local development?
root.keyis the private key of the server that wants to be secured.root.crtis the root certificate of the server that wants to be secured.kafka.keystore.jksis for the server that wants to be secured.kafka-signing-request.crtis the CSR from the server to the local CSA.kafka-signed.crtis the signed certificate from the local CSA.- The server’s root certificate and the signed certificate from the CSA are imported into keystore. This is because, for development purposes, we also the secured server. The secured server’s keystore needs to have the root certificate and the signed certificate imported.
- We also import the root certificate into the trust store. This is because, for development purposes, we are also the client application. So, the client application’s trust store needs to have the root certificate.